There’s an Ars Technica article flying around right now about a massive attack on wordpress sites around the internet attempting to build a super botnet. The attack is working by targeting a particular user account that the vast majority of sites have, including this one.
According to CloudFlare’s Prince, the distributed attacks are attempting to brute force the administrative portals of WordPress servers, employing the username “admin” and 1,000 or so common passwords.
User access to wordpress relies on knowing three things. A user id, a password, and a login location. This attack is assuming that there will be an administrator account with the user id admin, and is then firing a brute force attack trying to decode the password. Advice to change your password is not necessarily going to help – it might be that your password of choice is one of the 1000 common ones being used as mentioned above. If you go for a long password with a mixture of letters, number and characters you’re going to be much safer. But if you get rid of the account called admin, you’re going to be immune to this particular attack at least.
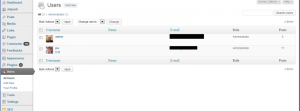
First thing to do, check if you’ve got an admin account. Go into your dashboard, select users> all users. You should see something a bit like this. (As ever, click to see it larger.)
As you can see, I do indeed have an admin account. It will have a strong password – we have a rule that passwords must be at least 8 characters with a mix of numbers, letters and characters. But I’ve decided we’re going to get rid of it anyway.
Step one – create a new administrator level account. If you’ve only got one email address to play with, you’re going to have to take it out of the existing admin account before you can create the new one. Make sure you give the new account a strong password that you can remember.
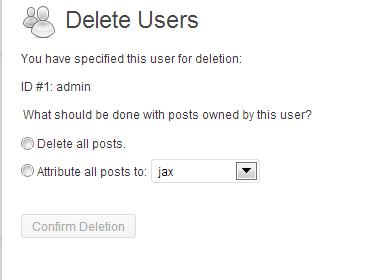
Step two – log in with the new account. Delete the existing admin account. You might be worrying about what will happen to posts associated with that account – don’t. You’ll get this dialog up with the choice of who to attribute them to. Pass them to your new user.
And there you go. You now have a wordpress installation without the admin account currently under attack across the internet.
Of course, that’s nowhere near the only thing you can do to protect your beloved blog/website, but it’s an excellent starting point. If you want to go into more detail, you might want to explore a security plugin like this one which will, among other things, allow you to rename the admin account without going through the process I’ve detailed here. And the other thing that’s important to do is keep your theme and plugins updated. Like I’m just about to.
If you’ve found this article helpful, please feel free to share it, and subscribe to my blog. Thanks for dropping by.
This was a massive help for me, I’be just followed your instructions and feel a lot better! Thank you as always 🙂 Caroline.
Glad to help.
If you’re technologically minded you can also rename the admin account in phpmyadmin 🙂
You can, but unless you’re technologically minded I’d advise against it 😉
Even though its been a little while, I went in and did this just in case. Thanks!
Thank you! All done now.I’ll share your link after the school run.
During setup I make a point of renaming the admin account so I don’t have this sort of trouble later on.
Good advice for when people are setting up from scratch, but there are an awful lot of vulnerable installations out there already.